CI/CD Integration using Personal token
Integrate Zephyr Cloud into your continuous integration and deployment pipelines to automate your deployment workflow. This guide covers setup for GitHub Actions and GitLab CI/CD.
Personal tokens authenticate as individual users. For organization-level authentication in CI/CD, consider using Server Tokens instead. Server tokens provide centralized management and don't require individual user credentials. See the CI/CD Server Token guide for details.
Overview
Generate an API Token
To use Zephyr Cloud in CI/CD pipelines, you'll need an API token for authentication:
Click on your avatar
In the upper right you should see your user's avatar with a dropdown menu
Select My Profile
One of the options in this menu should be "My Profile"
Select the settings tab
Once on the profile page, select the settings tab from the tab options
Select API Tokens from the left navigation
On the left hand navigation there should be an option for "API Token" - select this option
Click Generate Token Button
Fill out the required information about the token you're about to generate
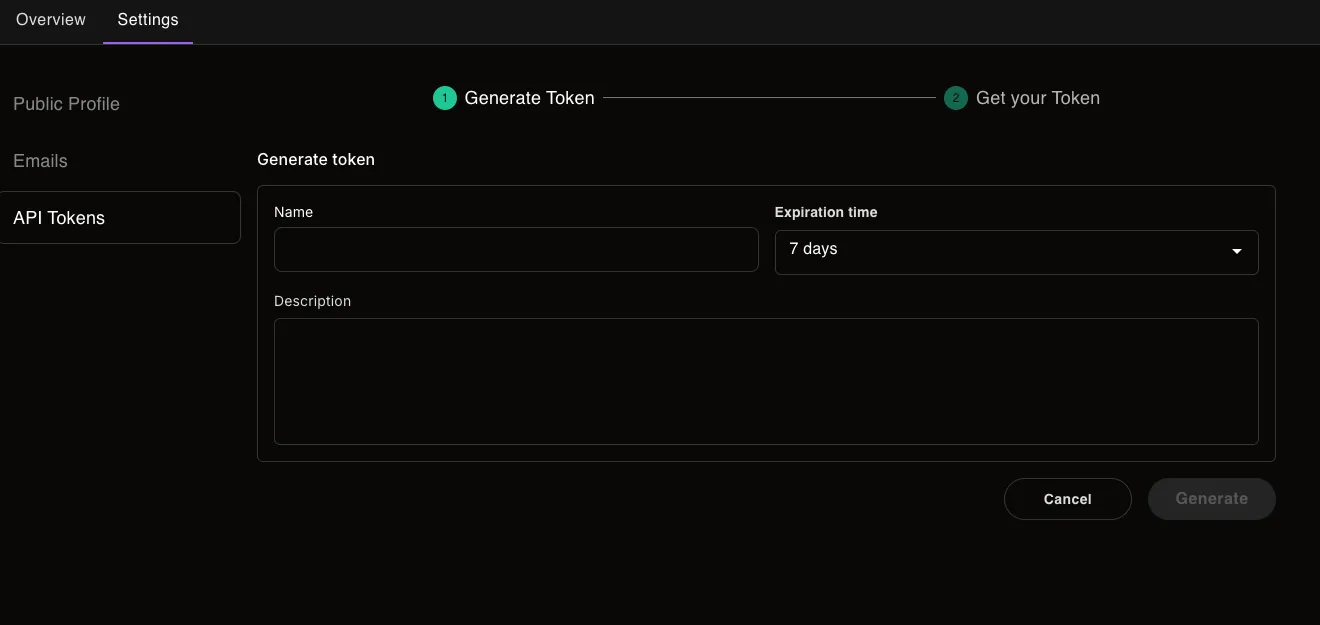
Click Generate
Copy the token for usage where you need to use it
GitHub Actions
Zephyr requires an authenticated user to publish updates. Configure your GitHub Actions pipeline to build and deploy with Zephyr by adding a token to your repository secrets.
Adding the GitHub Secret
- Create a token on your API token page
- Add it as a repository secret in GitHub
- The secret must be assigned to the
ZE_SECRET_TOKENenvironment variable
Authentication Behavior
When the Zephyr plugin detects the ZE_SECRET_TOKEN environment variable, it will automatically authenticate with the Zephyr API, bypassing the usual login step.
You'll see this confirmation in the console:
GitLab CI/CD
Configure your GitLab Runner pipeline to build and deploy with Zephyr by adding a token to the CI/CD variables.
Adding the GitLab CI/CD Variable
- Create a full access token on your API token page
- Add it as a CI/CD variable in your GitLab project:
Steps to add the token:
- Navigate to your GitLab project
- Go to Settings → CI/CD
- Expand the Variables section
- Click Add variable
- Configure the variable:
- Key:
ZE_SECRET_TOKEN - Value: Your Zephyr API token
- Type: Variable
- Environment scope: All (or specify specific environments)
- Protect variable: ✅ Check if you want to use it only in protected branches
- Mask variable: ✅ Check to hide the value in job logs
- Key:
Using the Token in GitLab CI/CD
In your .gitlab-ci.yml file, the token will be automatically available as an environment variable:
For more explicit control, you can also reference it directly:
Authentication Behavior
When the Zephyr plugin detects the ZE_SECRET_TOKEN environment variable, it will automatically authenticate with the Zephyr API, bypassing the usual login step.
You'll see this confirmation in the console:
Complete Pipeline Example
Here's a full GitLab CI/CD pipeline configured for Zephyr deployment:
Troubleshooting
Authentication Issues
Token not found error:
- Verify the variable name is exactly
ZE_SECRET_TOKEN - Ensure the variable is available in the environment where your job runs
- Check that the token hasn't expired
GitLab-Specific Issues
Protected variables:
- If using protected variables, ensure your pipeline runs on a protected branch or tag
Masked variables:
- Masked variables won't appear in job logs (recommended for security)
- Temporarily unmask if you need to troubleshoot, then re-mask for production
Variable scope:
- Check that the variable scope matches your pipeline's environment requirements
Related Documentation
CI/CD & Deployment:
- Server Token CI/CD Integration - Organization-level authentication for CI/CD
- Automation - Automated workflows and deployment strategies
- Tags & Environments - Managing deployment targets
Getting Started:
- Quick Start - Initial setup and first deployment
- Integration Guides - Adding Zephyr to existing applications